| Status | ||||
|---|---|---|---|---|
|
| Table of Contents |
|---|
Team
| Name | Organization | Role | |
|---|---|---|---|
| Dimitris Mavrommatis | ONF / Foundation for Research and Technology - Hellas (FORTH), Institute of Computer Science, INSPIRE group | Lead Developer | dimitris@opennetworking.org |
| Lefteris Manassakis | Foundation for Research and Technology - Hellas (FORTH), Institute of Computer Science, INSPIRE group | Engineering Supervisor / | |
| Vasileios Kotronis | Foundation for Research and Technology - Hellas (FORTH), Institute of Computer Science, INSPIRE group | Research Supervisor / | vkotronis@ics.forth.gr |
...
Basic knowledge of the BGP protocol and its best path selection algorithm is required in order to fully grasp the concepts behind ARTEMIS. However, everyone with basic ONOS[15] and mininet[11] skills can follow the demo without this prior knowledge.
...
| Code Block | ||
|---|---|---|
| ||
"org.onosproject.artemis" : {
"artemis" : {
"prefixes" : [
{
"prefixmoas": : "40.0.0.0/8"[ ],
"paths" : [
{
"originneighbor" : 65004,[
"neighbor" : [{
{
"asn" : 65002,
"neighbor": [
65001 ]
}
65001
]
]
}
],
}
"moas" : [ ]
}],
],
"frequency" : 3000,
"monitorsorigin" : {65004
"ripe" : [ }
],
"exabgp "prefix": [ "19240.1680.1.2:5000" ]
0.0/8"
}
}
} |
Explanation of fields
]
},
"moas": { },
"monitors": {
"exabgp": [
"192.168.1.2:5000"
],
"ripe": []
}
}
} |
Explanation of fields
prefixes:List consisting of prefixes with their AS-PATH information and (optionally) legitimate MOAS ASes.
prefix: a CIDR representation of the prefix that is monitored/protected.
paths: a list of dictionaries that contain the ASN of the protected AS (origin), along with a list of dictionaries for the neighbors.
neighbor: list of
prefix: a CIDR representation of the prefix that is monitored/protected.
paths: a list of dictionaries that contain the ASN of the protected AS (origin), along with a list of dictionaries for the neighbors.
neighbor: list of dictionaries that contain each neighbor's ASN and a list of ASNs for the neighbor's neighbor.
For example, in the demo topology the protected (origin) AS65004 sees the AS65002 as a first-hop neighbor, and AS65001 as a second-hop neighbor (resulting in the legitimate announced path AS65004 - AS65002 - AS65001).
Note: While the operator can supply the origin and first-hop neighbor ASNs as ground-truth in the configuration, the N-hop (N > 1) neighbor information is planned to be generated automatically by ARTEMIS in future versions of the tool, based on the received BGP updates.moas: *in-progress*
frequencymoas:Polling interval in milliseconds for the detection mechanism to check batches of BGP update messages (stored in the application cache). In the demo configuration file, it is set to check every 3s (3000ms). *in-progress*
monitors: List of the route collectors that ARTEMIS is using for monitoring. Currently it supports RIPE and ExaBGP route collectors through the socket-io interface, and is extendable to include more monitoring services/APIs.
RIPE Route Collectors have specific identifiers ("rrc17rrc18", "rrc18rrc19", "rrc19rrc20", "rrc20rrc21"). You can configure them following this example: "ripe" : ["rrc17rrc18", "rrc19"]
An ExaBGP Route Collector (RC) is implemented inside the tutorial folder (/onos/tools/tutorials/artemis/). You can host such an RC locally by running an ExaBGP instance with the exabgp.conf and server.py files provided (will require modifications in directory paths). In the demo topology we have an ExaBGP speaker running on 192.168.1.2:5000, monitoring the BGP control plane from the perspective of AS65001.
...
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ cd ~ $ sudo apt-get install git $ git clone -b 3.4 https://github.com/Exa-Networks/exabgp $ cd exabgp; git checkout 3.4 $ echo 'export PATH=$PATH:~/exabgp/sbin' >> ~/.bashrc $ source ~/.bashrc |
...
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ cd ~ $ sudo apt-get install software-properties-common -y && \ sudo add-apt-repository ppa:webupd8team/java -y && \ sudo apt-get update && \ echo "oracle-java8-installer shared/accepted-oracle-license-v1-1 select true" | sudo debconf-set-selections && \ sudo apt-get install oracle-java8-installer oracle-java8-set-default -ylicense-v1-1 select true" | sudo debconf-set-selections && \ sudo apt-get install oracle-java8-installer oracle-java8-set-default -y |
Download ONOS from GitHub and configure the corresponding bash profile:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ git clone https://github.com/opennetworkinglab/onos.git
$ echo '. ~/onos/tools/dev/bash_profile' >> ~/.bashrc
$ source ~/.bashrc |
Install pip3, Python packages and set the configuration used by ExaBGP:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ sudo apt-get install python3-pip -y
$ sudo -H pip3 install -r ~/onos/tools/tutorials/artemis/requirements.txt
$ cd ~/onos/tools/tutorials/artemis/
$ sed -i 's?/absolute/path/to/onos/tools/tutorials/artemis?'`pwd`'?' configs/exabgp.conf |
You must verify that the run command in config file now has the absolute path, e.g., /home/user/onos/tools/tutorials/artemis/server.py.
Verify the path that is specific to your setup, using cd and/or pwd/ls, as shown in Figure 3:
Fig. 3: Verifying the absolute path for the exaBGP configuration file (exabgp.conf).
Install curl and run ONOS (the first run will require some time):
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ sudo apt-get install curl
$ cd onos
$ buck run onos-local -- clean |
After the ONOS instance has started, open a new terminal and load the mininet topologyDownload ONOS from GitHub and configure the corresponding bash profile:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ git clone https://github.com/opennetworkinglab/onos.git $ echo '. ~/cd onos/tools/dev/bash_profile' >> ~/.bashrctutorials/artemis $ sourcesudo ~./artemis-topo.bashrcpy |
While having the two terminals open (ONOS instance and mininet), open a new terminal and load the network configuration with onos-netcfg. From this terminal, login to the ONOS CLI:Install pip3, Python packages and set the configuration used by ExaBGP:
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
$ onos-netcfg localhost$ sudo apt-get install python3-pip -y $ sudo -H pip3 install -r ~/onos/tools/tutorials/artemis/requirements.txt $ nano ~/onos/tools/tutorials/artemis/configs/exabgp.conf |
You must put the absolute path at the run command, e.g., /home/user/onos/tools/tutorials/artemis/server.py.
Verify the path that is specific to your setup, using cd and/or pwd/ls, as shown in Figure 3:
Fig. 3: Verifying the absolute path for the exaBGP configuration file (exabgp.conf).
network-cfg.json
$ onos localhost |
On your monitor, you should see a view similar to Figure 4:
Fig. 4: ONOS instance, mininet and ONOS CLI.
Activate ARTEMIS using the ONOS CLI (reactive-routing must be activated firstInstall curl and run ONOS (the first run will require some time):
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ sudo apt-get install curl
$ cd onos
$ buck run onos-local -- clean | ||||
onos> app activate org.onosproject.reactive-routing
onos> app activate org.onosproject.artemis |
Check if bgp-routes are visible by ONOS, indicating that BGP has converged (must include the 10.0.0.0/8, 20.0.0.0/8, 30.0.0.0/8 and 40.0.0.0/8 prefixes; if not, you should restart the mininet topology). It requires time (~1-2 minutes) for the BGP protocol to converge, so this step requires patienceAfter the ONOS instance has started, open a new terminal and load the mininet topology:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ cd onos/tools/tutorials/artemis
$ sudo ./topo.py | ||||
ONOS> bgp-routes |
Now that the topology is running, through the mininet CLI you can connect to the hosts to check connectivity and also to the BGP speakers to modify the BGP control plane. To hijack the prefix of the protected AS:
1. Connect to the BGP speaker named R3, and also check connectivity between hosts H1 and H4: While having the two terminals open (ONOS instance and mininet), open a new terminal and load the network configuration with onos-netcfg. From this terminal, login to the ONOS CLI:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ onos-netcfg localhost ~/onos/tools/tutorials/artemis/configs/network-cfg.json
$ onos localhost |
On your monitor, you should see a view similar to Figure 4:
Fig. 4: ONOS instance, mininet and ONOS CLI.
mininet> xterm R3 (opens a new terminal on R3)
mininet> pingall (to make the hosts visible)
mininet> h1 ping h4 (to see the data plane interactions) |
2. On the terminal of R3, announce the prefixActivate ARTEMIS using the ONOS CLI (reactive-routing must be activated first):
| Code Block | ||||
|---|---|---|---|---|
| ||||
onos> app activate org.onosproject.reactive-routing
onos> app activate org.onosproject.artemis |
...
R3> telnet localhost bgpd Password: sdnip (this is the password) bgp> en (enable) bgp# conf t (configure terminal) bgp(config)# router bgp 65003 bgp(config-router)# network 40.0.0.0/8 |
Now the hijacker (AS65003) will attract all the traffic from AS65001 (destined to , 20.0.0.0/8, 30.0.0.0/8 and 40.0.0.0/8 prefixes; if not, you should restart the mininet topology). It requires time (~1-2 minutes) for the BGP protocol to converge, so this step requires patience:
| Code Block | ||||
|---|---|---|---|---|
| ||||
ONOS> bgp-routes |
Now that the topology is running, through the mininet CLI you can connect to the hosts to check connectivity and also to the BGP speakers to modify the BGP control plane. To hijack the prefix of the protected AS:
1. Connect to the BGP speaker named R3, and also check connectivity between hosts H1 and H4:
| Code Block | ||||
|---|---|---|---|---|
| ||||
mininet> xterm R3 (opens a new terminal on R3)
mininet> pingall (to make the hosts visible)
mininet> h1 ping h4 (to see the data plane interactions) |
) away from AS65004; at the same time, the ExaBGP speaker in AS65001 will send the BGP update of the hijack (among other updates seen by AS65004) to the ONOS instance (running ARTEMIS) and the hijack will be detected. Observing the ONOS logs, you will see that the attack is actually detected and the deaggregation mechanism has successfully mitigated the attack (by announcing the more specific prefixes 40.0.0.0/9 and 40.128.0.0/9 from the BGP speaker of the protected AS). After BGP converges and the control and data planes are consistent, the traffic of AS65001, destined to 40.0.0.0/8, returns to the protected AS, as shown in Figure 5:
Fig. 5: Successful mitigation of the BGP prefix hijacking attack, with a data loss of only 4 packets.
3. Also, by checking the current configuration of R42. On the terminal of R3, announce the prefix:
| Code Block | ||||
|---|---|---|---|---|
| ||||
R3>mininet> xterm R4 (opens a new terminal on R4) R4> telnet localhost bgpd Password: sdnip (this is the password) bgp> en (enable) bgp# confsh trun (configure terminal) bgp(config)# router bgp 65003 bgp(config-router)# network 40.0.0.0/8 |
Now the hijacker (AS65003) will attract all the traffic from AS65001 (destined to 40.0.0.0/8) away from AS65004; at the same time, the ExaBGP speaker in AS65001 will send the BGP update of the hijack (among other updates seen by AS65004) to the ONOS instance (running ARTEMIS) and the hijack will be detected. Observing the ONOS logs, you will see that the attack is actually detected and the deaggregation mechanism has successfully mitigated the attack (by announcing the more specific prefixes 40.0.0.0/9 and 40.128.0.0/9 from the BGP speaker of the protected AS). After BGP converges and the control and data planes are consistent, the traffic of AS65001, destined to 40.0.0.0/8, returns to the protected AS, as shown in Figure 5:
Fig. 5: Successful mitigation of the BGP prefix hijacking attack, with a data loss of only 4 packets.
3. Also, by checking the current configuration of R4:
| Code Block | ||||
|---|---|---|---|---|
| ||||
mininet> xterm R4 (opens a new terminal on R4)
R4> telnet localhost bgpd
Password: sdnip (this is the password)
bgp> en (enable)
bgp# sh run (show running configuration) |
We observe that ARTEMIS has automatically configured R4 to announce the more specific prefixes 40.0.0.0/9 and 40.128.0.0/9, thus mitigating the attack, as shown in Figure 6:
show running configuration) |
We observe that ARTEMIS has automatically configured R4 to announce the more specific prefixes 40.0.0.0/9 and 40.128.0.0/9, thus mitigating the attack, as shown in Figure 6:
Fig. 6: Current configuration of R4.
Frequently asked questions (FAQ)
Q: Why is the CLI output empty when I write bgp-routes in the ONOS CLI?
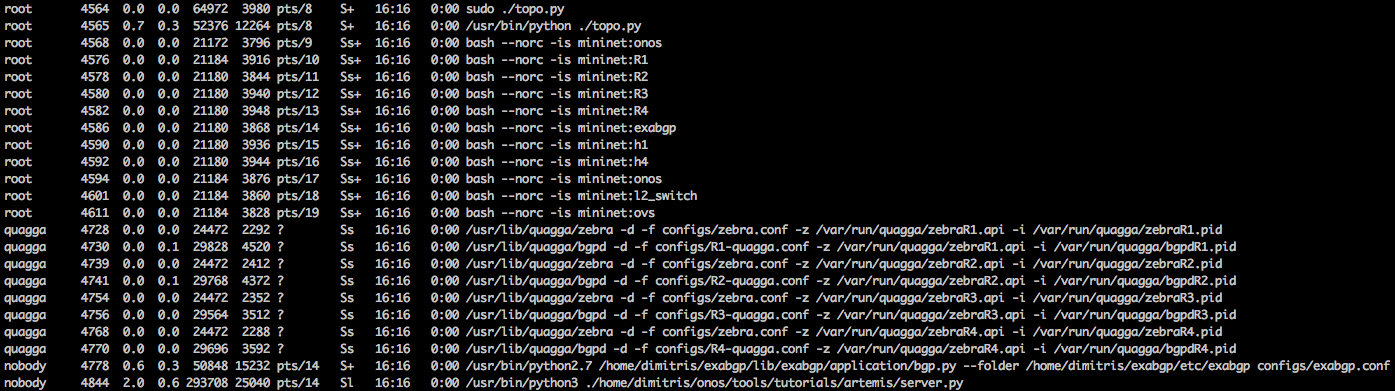
A: There might be multiple different problems that might cause this issue (e.g., Quagga not running or ExaBGP not running). To verify that everything is running correctly please run ps aux; the result should look as follows:
Also, there is a file inside the onos/tools/tutorials/artemis folder called exabgp.log. For ExaBGP to run successfully, the file should contain a line stating:
* Running on http://0.0.0.0:5000/ (Press CTRL+C to quit)
Q: Why am I getting an error when running the topology file?
A: You should check if the python3 requirements are installed correctly. Sometimes, the python deployment may consider the python3 package installed; it is though the python2 package instead. You could try installing again the dependency separately using pip3 install .
Q: All the processes run correctly but I still don't get the BGP routes to show; why?
A: This situation tends to happen if you have the networking manager enabled because sometimes it messes up the interfaces of the mininet topology. Please stop the network manager and restart the demo from scratchFig. 6: Current configuration of R4.
Future plans & extensions
Despite the fact that ARTEMIS was first tested in a non-SDN environment with the basic mitigation strategy of automatic prefix deaggregation in mind, it can support several extensions related to its monitoring, detection and mitigation mechanisms due to its modular design. These extensions, e.g., employing MOAS (Multi-Origin AS Announcements) and tunneling in order to steer the hijacked traffic back to its legitimate owner during the mitigation phase, will also be researched as extra modules built over the ONOS platform. In parallel to the mitigation, an additional monitoring service is envisioned to provide real-time information about the mitigation process. This service can also use data from Periscope, RIPE RIS, BGPstream and BGPmon to monitor/visualize the mitigation.
...