| Warning |
|---|
Page under construction |
| Table of Contents |
|---|
Team
| Name | Organization | Role | |
|---|---|---|---|
| Dimitris Mavrommatis | ON.Lab / Foundation for Research and Technology - Hellas (FORTH), Institute of Computer Science, INSPIRE group | Lead Developer | dimitris@onlab.us |
| Lefteris Manassakis | Foundation for Research and Technology - Hellas (FORTH), Institute of Computer Science, INSPIRE group | Engineering Supervisor / | |
| Vasileios Kotronis | Foundation for Research and Technology - Hellas (FORTH), Institute of Computer Science, INSPIRE group | Research Supervisor / | vkotronis@ics.forth.gr |
Overview and Goals
Prefix hijacking is a common phenomenon in the Internet that often causes routing problems and economic losses [13]. ARTEMIS [1,10] is a tool, usable by network administrators, to detect in real-time and automatically mitigate prefix hijacking incidents against their own prefixes, employing self-monitoring on the AS level. ARTEMIS employs real-time monitoring of BGP data (e.g., BGP updates exported by route collectors) and can: (a) detect a prefix hijacking within a few seconds from its launch, and (b) completely mitigate the hijack within a few minutes (e.g., 2-5 minutes in the initial experiments with the PEERING testbed [2]). This fast response time enables legitimate ASes to quickly counter the hijack based on data they observe themselves on the control plane.
The goal of this project is to implement ARTEMIS as a multi-module application running on top of ONOS [9], using the prior work and code-base of the SDN-IP project [3,8], as well as testing the application over a real BGP testbed such as PEERING [2]. The final objective is to have an open-source implementation of ARTEMIS running on top of a popular production-grade Network Operating System. This implementation will then enable researchers and operators to test miscellaneous BGP prefix mitigation strategies over real-world testbeds and production networks, and extract results that are relevant to today’s ISP operations; such results would be otherwise not possible to produce.
Prerequisites
Basic knowledge of the BGP protocol and its best path selection algorithm is required in order to fully understand the concepts of ARTEMIS. However, every user can try the demo without this prior knowledge.
ARTEMIS Architecture and Functionality
Fig. 1: The ARTEMIS architecture.
ARTEMIS consists of three components: a monitoring (1), a detection (2) and a mitigation (3) service as shown in Fig. 1.
1) The monitoring service runs continuously and provides control plane information from the AS itself, the streaming services of RIPE RIS [4] and BGPstream [6] (from RIPE RIS and RouteViews), as well as BGPmon [5] and Periscope [7], which return almost real-time BGP updates for a given list of prefixes and ASNs.
...
Note: Prefix deaggregation is effective for hijacks of IP prefixes less specific than /24, but it might not work for /24 prefixes or more specifics. This is because BGP advertisements of more specific than /24 prefixes are typically filtered by many ISPs, since it is considered as best practice to avoid the exponential increase of the size of the BGP routing table. We plan to address this problem through future extensions of ARTEMIS (e.g., collaborative mitigation).
Fig. 1: The ARTEMIS architecture.
Future plans: Despite the fact that ARTEMIS was first tested in a non-SDN environment with the basic mitigation strategy of automatic prefix deaggregation in mind, it can support several extensions related to its monitoring, detection and mitigation mechanisms due to its modular design. These extensions, e.g., employing MOAS (Multi-Origin AS Announcements) and tunneling in order to steer the hijacked traffic back to its legitimate owner during the mitigation phase, will also be researched as extra modules built over the ONOS platform. In parallel to the mitigation, an additional monitoring service is envisioned to provide real-time information about the mitigation process. This service can also use data from Periscope, RIPE RIS, BGPstream and BGPmon to monitor/visualize the mitigation.
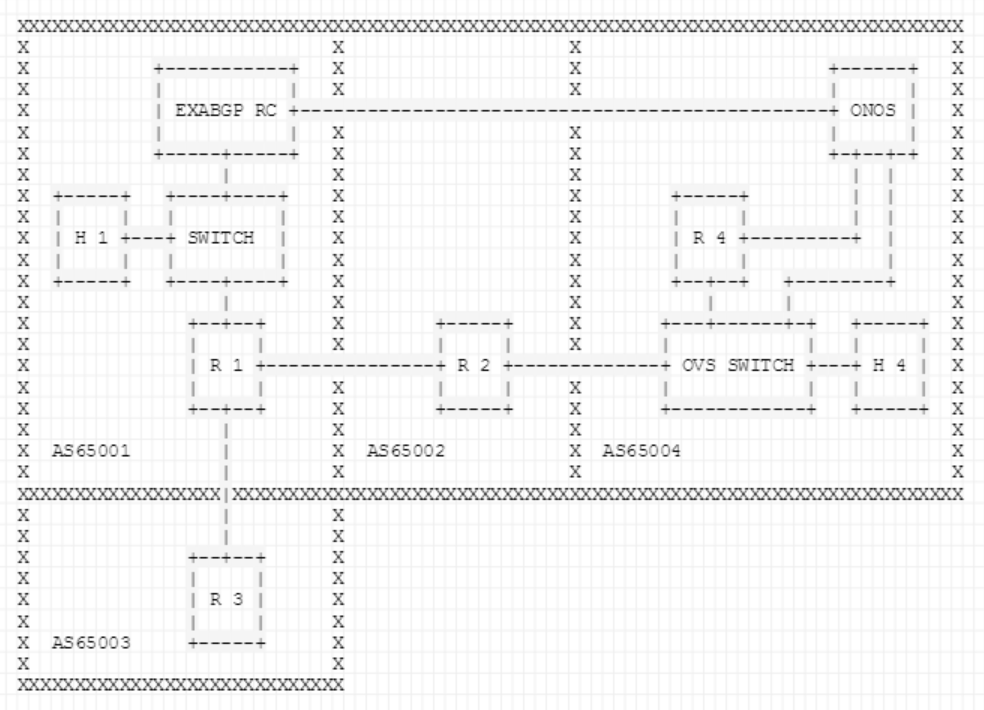
Demo Topology
Figures Figures 2 and 3 show the topology that is setup via the topo.py file inside the tutorial folder (TODO: set exact location). The BGP speakers are Quagga routers and the route collector is an ExaBGP router running a custom script to replicate the behavior of a RIPE route collector.
...
...
Fig. 3: The full emulated demo topology.
...
AS65002
Intermediate AS that consists of a BGP speaker (R2) that announces 20.0.0.0/8 and its purpose is to add an additional hop to the AS-PATH so that the protected AS can be hijacked. Although in the demo the attacker announces the exact prefix that belongs to the protected AS and not a more specific one, due to the shortest path attribute of the BGP best path selection algorithm, is able to steal the traffic.AS65003
Hijacker AS that consists of a BGP speaker (R3).R3: By announcing the prefix of the protected AS (40.0.0.0/8) from this BGP speaker, we trigger a BGP hijack, and all traffic generated from AS65001 and directed towards AS65004, will be redirected to the network of AS65003.
AS65004
Protected AS that is employing ONOS. It consists of a BGP speaker, an OVS switch, a host and the ONOS instance.R4: BGP speaker announcing 40.0.0.0/8. It is connected with his neighbor through the OVS switch which is configured by the SDN-IP application to talk with the BGP speaker of AS65002.
OVS: Talks with ONOS on a management interface via 192.168.0.0/24.
ONOS: ONOS is connected with the BGP speaker to retrieve the BGP routing table. Also, it receives the BGP update messages from the ExaBGP router. Also, it has a link with the OVS switch in order to interact with the data plane.
- H4 / 40.0.0.100: Host that receives traffic with the help of the reactive-routing application from the host in AS65001.
JSON Configuration File
The JSON Configuration File is the file that contains the required configuration entries to monitor prefixes and check the validity of neighbors and paths. The following code block shows an example of the JSON configuration format for ARTEMIS which is used in the Demo Topology.
...
Note: The demo configuration also includes entries for the SDN-IP and the Reactive-Routing application (separate step, not shown in this demo). It specifies where the BGP speaker is located and which are the local prefixes.
Running the Demo
Install the ExaBGP Python library by doing these steps:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ cd ~ $ git clone https://github.com/Exa-Networks/exabgp $ cd exabgp; git checkout 3.4 $ echo 'export PATH=$PATH:~/exabgp/sbin' >> ~/.bashrc $ source ~/.bashrc |
Install the Quagga software routing suite through apt-get:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ sudo apt-get install quagga -y |
Download and install the mininet emulation platform:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ cd ~ $ git clone https://github.com/mininet/mininet $ cd mininet; git checkout 2.2.2 $ ./util/install.sh -fnv |
Install java 8 (needed required by ONOS in the next steps):
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ sudo apt-get install software-properties-common -y && \ sudo add-apt-repository ppa:webupd8team/java -y && \ sudo apt-get update && \ echo "oracle-java8-installer shared/accepted-oracle-license-v1-1 select true" | sudo debconf-set-selections && \ sudo apt-get install oracle-java8-installer oracle-java8-set-default -y |
Download ONOS from GitHub and add configure the bash profile:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ cd ~ $ git clone https://github.com/opennetworkinglab/onos.git $ echo '. ~/onos/tools/dev/bash_profile' >> ~/.bashrc $ source ~/.bashrc |
...
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ sudo apt-get install python3-pip -y $ sudo pip3 install -r ~/onos/tools/tutorials/artemis/requirements.txt $ nano ~/onos/tools/tutorials/artemis/configs/exabgp.conf (you must put the absolute path at run command, e.g., /home/onos/onos/tools/tutorials/artemis/server.py) |
Run ONOS (the first time run will take some require more time):
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ buck run onos-local -- clean |
...
Note: If you are using a GUI version of Ubuntu, you should disable networking by un-checking unchecking it in the relevant menu, in order to avoid interfaces swapping IP addresses!
Pass Load the network configuration with onos-netcfg and login to the onos CLI:
| Code Block | ||||
|---|---|---|---|---|
| ||||
$ onos-netcfg localhost ~/onos/tools/tutorials/artemis/configs/network-cfg.json $ onos localhost |
Run artemis inside Activate ARTEMIS using the ONOS CLI (requires reactive-routing as a prerequisite applicationmust be activated first):
| Code Block | ||||
|---|---|---|---|---|
| ||||
onos> app activate org.onosproject.reactive-routing onos> app activate org.onosproject.artemis |
Check if bgp-routes are complete (should include visible by ONOS, indicating that BGP has converged (must include the 10.0.0.0/8, 20.0.0.0/8, 30.0.0.0/8 and 40.0.0.0/8 prefixes; if not, you should restart the topology. It takes some requires time (~1-2min) for the BGP protocol to converge):
| Code Block | ||||
|---|---|---|---|---|
| ||||
ONOS> bgp-routes |
...
Now the hijacker (AS65003) will attract all the traffic away from AS65001 (destined to 40.0.0.0/8); in parallel at the same time, the ExaBGP speaker will send the BGP update of the hijack (among other updates seen by AS65004) to the ONOS instance (running artemis) which is going to detect ARTEMIS) and the hijack will be detected. Inside Checking the logs, you will see that the attack is actually detected and the deaggregation mechanism has successfully mitigated the attack (by announcing the more specific prefixes 40.0.0.0/9 and 40.128.0.0/9 from the BGP speaker of the protected AS). After BGP converges and the control and data planes are consistent, the traffic of AS65001, destined to 40.0.0.0/8, returns to the protected AS.
Demo video
| Widget Connector | ||
|---|---|---|
|
ONOS Technical Steering Team Presentation
| Widget Connector | ||
|---|---|---|
|
...
[2] “About PEERING - The BGP TetsbedTestbed”, https://peering.usc.edu/
...